the following special forms using leading or trailing
underscores are recognized (these can generally be combined with any case
convention):
- _single_leading_underscore: weak "internal use" indicator. E.g. "from M
import *" does not import objects whose name starts with an underscore.
- single_trailing_underscore_: used by convention to avoid conflicts with
Python keyword, e.g.
Tkinter.Toplevel(master, class_='ClassName')
- __double_leading_underscore: when naming a class attribute, invokes name
mangling (inside class FooBar, __boo becomes _FooBar__boo; see below).
- __double_leading_and_trailing_underscore__: "magic" objects or
attributes that live in user-controlled namespaces. E.g. __init__,
__import__ or __file__. Never invent such names; only use them
as documented.Sunday, June 30, 2013
Underscores in Python
Tuesday, June 25, 2013
HTML Notes
Overlay one div on another div
#div_1 {
position: absolute;
}
thus the two div_1 is overlaid on div_2
Friday, June 21, 2013
Cannot Sleep? Association Rule Can Help You
Stimulus Control Therapy
- Lie down to go to sleep only when you are sleepy.
- Do not use your bed for anything except sleep; that is, do not read, watch television, eat, or worry in bed. Sexual activity is the only exception to this rule. On such occasions, the instructions are to be followed afterwards, when you intend to go to sleep.
- If you find yourself unable to fall asleep, get up and go into another room. Stay up as long as you wish and then return to the bedroom to sleep. Although we do not want you to watch the clock, we want you to get out of bed if you do not fall asleep immediately. Remember the goal is to associate your bed with falling asleep quickly! If you are in bed more than about 10 minutes without falling asleep and have not gotten up, you are not following this instruction.
- If you still cannot fall asleep, repeat step 3. Do this as often as is necessary throughout the night.
- Set your alarm and get up at the same time every morning irrespective of how much sleep you got during the night. This will help your body acquire a consistent sleep rhythm.
- Do not nap during the day.
Notes on Memory
How Memory Works: 10 Things Most People Get Wrong

"If we remembered everything we should on most occasions be as ill off as if we remembered nothing." ~William James
Change the size of Thumbnail Preview. Aero Peek

Make the Taskbar Thumbnail Preview Bigger in Windows 7
Source: http://www.winhelponline.com/blog/increase-taskbar-thumbnail-preview-size-windows-7/
Thursday, June 20, 2013
Wednesday, June 19, 2013
Regular Expression (Regexe)
yet another insignificant Programming Notes
Regular Expression
Regular Expression, or regexe in short, is extremely and amazingly powerful in searching and manipulating text strings. One line of regexe can easily replace several dozen lines of programming codes. Regexe is supported in almost all the scripting languages (such as Perl, Python, PHP, and JavaScript) as well as general purpose programming languages such as Java, and even word processor such as Word for searching texts.>>> convert('CamelCase')
camel_caseTuesday, June 18, 2013
C++ & Java: args and argv
aAutoDeleteEnginePath = AdaConstants.AUTODELETE_BIN_PATH; aAutoDeleteEngineOutputFilePath = AdaConstants.AUTODELETE_OUTPUT_FILE_PATH; aTerminal = args[0]; aTimestamp = args[1];C++ the argv[0] is the command itself java the args[0] is the first argument
Sunday, June 16, 2013
Saturday, June 15, 2013
ERP Implementation Cases Reflection
Zhang Danyang
Overview
Overview
This reflection will discuss
about the lessons learned from both successful and unsuccessful Enterprise
Resource Planning (ERP) implementation cases. The purpose of ERP is to
integrate and unify every aspect of the business of an enterprise into one
single suite of software system. Many of the ERP implementation cases occurred
around late 1990’s, in an attempt to tackle with Y2K problems. After discussion about the lessons learned
from these cases, the reflection will talk about the ERP implementation approaches,
and a new approach from Software Engineering is proposed.
Recommend a Plagiarism Checking Website
Friday, June 14, 2013
The Tipping Point (Malcolm Gladwell) -- Summary of Info on Wikipedia
Hub in Information Dissemination
Some of Malcolm Gladwell's analysis as to why the phenomenon of the "tipping point" occurs (particularly in relation to his idea of the "law of the few") and its unpredictable elements[16] is based on the 1967 small-world experiment by social psychologist Stanley Milgram. Milgram distributed letters to 160 students in Nebraska, with instructions that they be sent to a stockbroker in Boston (not personally known to them) by passing the letters to anyone else that they believed to be socially closer to the target. The study found that it took an average of six links to deliver each letter. Of particular interest to Gladwell was the finding that just three friends of the stockbroker provided the final link for half of the letters that arrived successfully.[17] This gave rise to Gladwell's theory that certain types of people are key to the dissemination of information.
Outliers (Malcolm Gladwell) -- Summary of Info on Wikipedia
Christopher Langan and J. Robert Oppenheimer, end up with such vastly different fortunes.
All Gladwell's books focus on singularities: singular events in The Tipping Point, singular moments in Blink, and singular people in Outliers. Gladwell was drawn to writing about singular things after he discovered that "they always made the best stories".[1] Convinced that the most unusual stories had the best chance of reaching the front page of a newspaper, he was "quickly weaned off the notion that [he] should be interested in the mundane".[1]
Wednesday, June 12, 2013
C++ file IO
freopen("input.txt","r",stdin);
string line;
stringstream ss;
getline(cin, line);
while(line!=""){
ss<
Tuesday, June 11, 2013
Euler Project Question #3
Euler Project Question #3
Find Prime:
We can use the Fundamental Theorem of Arithmetic which states:
Any integer greater than 1 is either a prime number, or can be written as a unique product of prime numbers (ignoring the order).
Any integer greater than 1 is either a prime number, or can be written as a unique product of prime numbers (ignoring the order).
Windows Basics CMD Shell & Others
1. Frequently-used Commands
General Notes: The commands are NOT case-sensitive (because the legacy DOS is not case-sensitive). In general, Windows/DOS Operating System is not case-sensitive, but Unixes are. Most of the programming languages such as C/C++/Java, with origin in Unix, are case-sensitive.
1.1 Help
Help: To list all the available commands, for example,
1.2 Directory- and File-related Commands
Other frequently-used directory- and file-related commands include:
del filenames: Deletes files.ren current-filename new-filename: Renames a file.mkdir directory-name: Creates (or make) a sub-directory under the current working directory.rmdir directory-name: Removes or deletes the sub-directory.copy filename new-filename: Copies file.xcopy|robocopy: Copies (or Robust copies) files and directory trees.
Programmer's Survival Guide for Windows
2. Windows' File System and Basic File/Directory Commands
Windows' file system is NOT case-sensitive
Flow
familial relationships
collective form of TV watching
ostracization
funky clothes
demeanor
clique
expressivity
deferent waiter
bittersweet memories
spontaneous process
assiduously
dissipative
paraplegics
fulfilling
terminal illness
unwavering purpose
daunt
suspicion
epoch
Monday, June 10, 2013
Ubuntu Font on Chrome (Windows)
Three things:
1. Download Ubuntu Font Family
2. Install Ubuntu Font in Windows
3. Chrome Extension
1. Download Ubuntu Font Family
2. Install Ubuntu Font in Windows
3. Chrome Extension
1. Download Ubuntu Font Family
HTML 5 Semantic Element
http://www.w3schools.com/html/html5_semantic_elements.asp
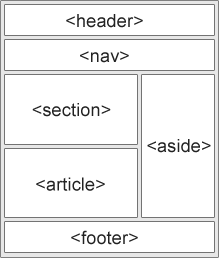
New Semantic Elements in HTML5
They are <div></div> by themselves
Many of existing web sites today contains HTML code like this: <div id="nav">, <div class="header">, or <div id="footer">, to indicate navigation links, header, and footer.
HTML5 offers new semantic elements to clearly define different parts of a web page:
- <header>
- <nav>
- <section>
- <article>
- <aside>
- <figcaption>
- <figure>
- <footer>

HTTP Response Error Codes
Error Codes
Because the default handlers handle redirects (codes in the 300 range), and codes in the 100-299 range indicate success, you will usually only see error codes in the 400-599 range.
C++ map::find() and map::operator[]
// map::find
#include <iostream>
#include <map>
urllib2 -- The Missing Mannual
urllib2 The Missing Mannual
Saturday, June 8, 2013
Reflection in Java (and a little Python)
toString(), iterates through every attributes in a Class
public class Formatter {
public static String toString(Object aObject) {
StringBuilder result = new StringBuilder();
String newLine = System.getProperty("line.separator");
result.append( aObject.getClass().getName() );
result.append( " Object {" );
result.append(newLine);
//determine fields declared in aObject class only (no fields of superclass)
Field[] fields = aObject.getClass().getDeclaredFields();
//print field names paired with their values
for ( Field field : fields ) {
result.append(" ");
try {
field.setAccessible(true);
result.append( field.getName() );
result.append(": ");
//requires access to private field:
result.append( field.get(aObject) );
} catch ( IllegalAccessException ex ) {
System.out.println(ex);
}
result.append(newLine);
}
result.append("}");
return result.toString();
}
}
Friday, June 7, 2013
Disable auto brightness/ dynamic contrast
- ctrl+alt+F12 to call up Intel Graphics->Power->On Battery->Max Performance, Plugged-in->Max Perforamnce
- Windows Advanced Power Options -> Display -> turn off "adaptive brightness"
- If it does not work, try to plug and unplug the power supply several times.
Java Serialization Tutorial
source: http://www.tutorialspoint.com/java/java_serialization.htm
like pickle in Python:
Java provides a mechanism, called object serialization where an object can be represented as a sequence of bytes that includes the object's data as well as information about the object's type and the types of data stored in the object.
like pickle in Python:
Java provides a mechanism, called object serialization where an object can be represented as a sequence of bytes that includes the object's data as well as information about the object's type and the types of data stored in the object.
Classes ObjectInputStream and ObjectOutputStream are high-level streams that contain the methods for serializing and deserializing an object.
Thursday, June 6, 2013
Permutation in Java and C++
C++
from #include<algorithm>
int a[] = {3,4,6,2,1};
int size = sizeof(a)/sizeof(a[0]);
std::sort(a, a+size);
do {
// print a's elements
} while(std::next_permutation(a, a+size));JAVA
public class Permute{
static void permute(java.util.List<Integer> arr, int k){
for(int i = k; i < arr.size(); i++){
java.util.Collections.swap(arr, i, k);
permute(arr, k+1);
java.util.Collections.swap(arr, k, i);
}
if (k == arr.size() -1){
System.out.println(java.util.Arrays.toString(arr.toArray()));
}
}
public static void main(String[] args){
Permute.permute(java.util.Arrays.asList(3,4,6,2,1), 0);
}
}
You take first element of an array (k=0) and exchange it with any element (i) of the array. Then you recursively apply permutation on array starting with second element. This way you get all permutations starting with i-th element. The tricky part is that after recursive call you must swap i-th element with first element back, otherwise you could get repeated values at the first spot. By swapping it back we restore order of elements (basically you do backtracking).
done
Subscribe to:
Posts (Atom)